The Concept of a Personal Portal
Back in 2000, I was thinking about how I could make my online life a little more convenient - and so the concept of the personal portal was born. This has been the root of my thinking and certain aspects of this are now a reality or at least a major consideration in the minds of those who are shaping the web and how we interact with it and within it.
As the internet becomes an undeniable and ubiquitous part of daily life, the personal portal becomes the individual's virtual persona on the web - acting as the single point of access to an individual's identity, preferences and history.
Information, the Individual and the Internet
The internet is rapidly becoming the predominant medium for both commercial and social information exchange. This exchange may be simple communication, social or business information provision or complex commercial transactions. Much of this information traffic has as its subject the individual - a data entity with many facets of information.
Information about the individual is created, stored and used by many parties with whom the individual deals with on a daily basis. Today the majority of this information is held on local databases and paper records, little is maintained on the web, however, as media converge, this information will migrate to web compatible media.
At this point all of the issues that organizations once played out when centralized computer systems were first proposed will re-surface: security, data duplication, maintaining the information as up to date and accessibility. This time, however, these issues will be applied to the individual.
The Concept of the Personal Portal
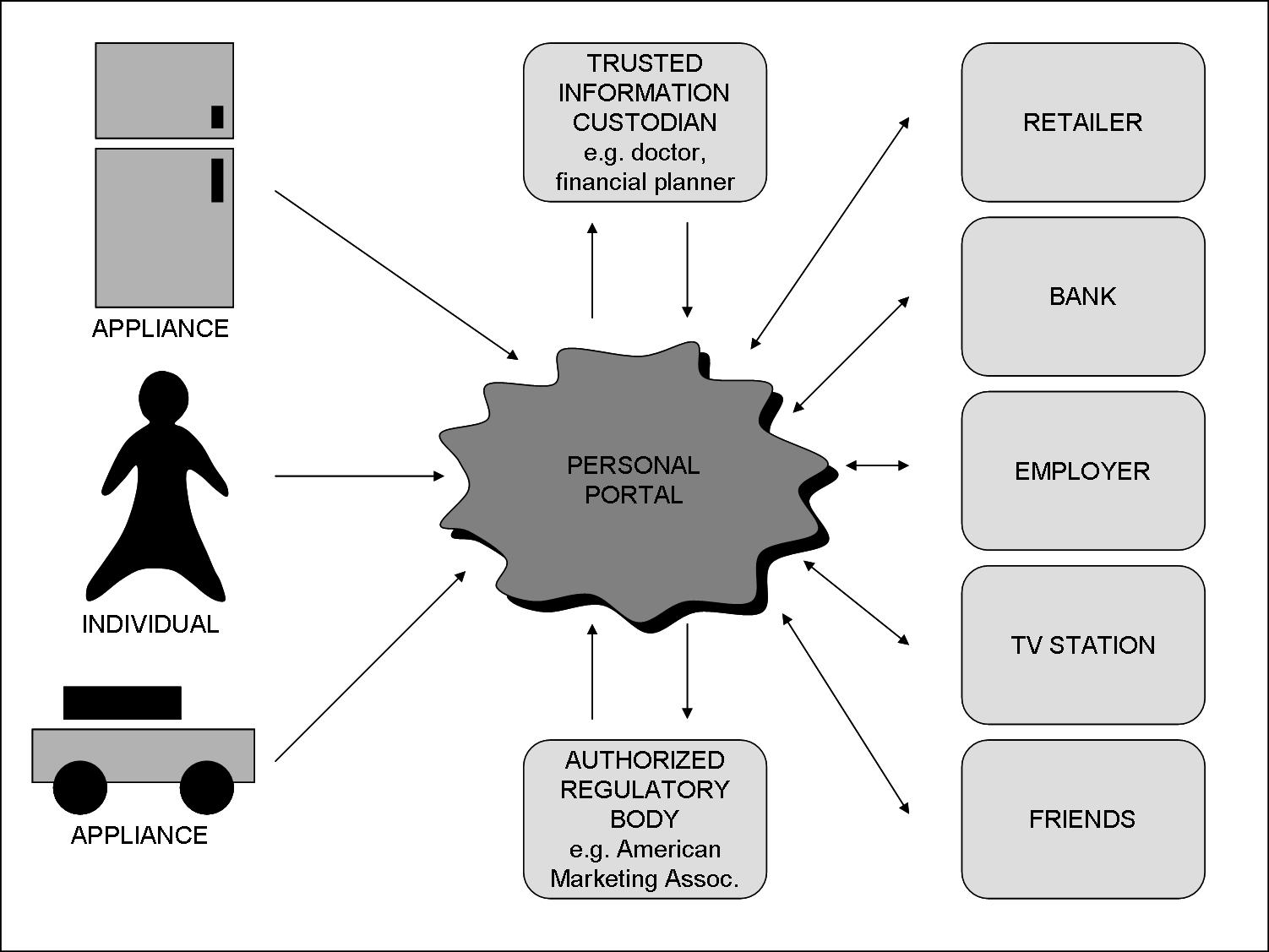
- A central repository of information about the individual held in a secure environment.
- The individual is able to maintain the information personally or to appoint trusted third parties to do so.
- The individual is able to give access to the information at a variety of levels to other parties who require it.
- All other parties who have not been granted specific access can request it or use public domain information distributed via third party information management agencies.
Commercial Implementation Realities
To bring the personal portals to market, it will be necessary to use organizations that have well-established trusted relationships with consumers such as banks or telephone companies. The model will follow that of the virtual ISP. Using this model, the end to end marketing of the personal portal will be managed by the consumer facing organizations. The level of security required will be relatively high, even at the personal device level (the personal portal will be accessed by all internet enabled devices).
Personal Information: one person, one place
As corporations strive towards the 'single view' and the internet breaks down the boundaries of organizations to embrace the real world, how come the data about an individual is maintained multiple times?
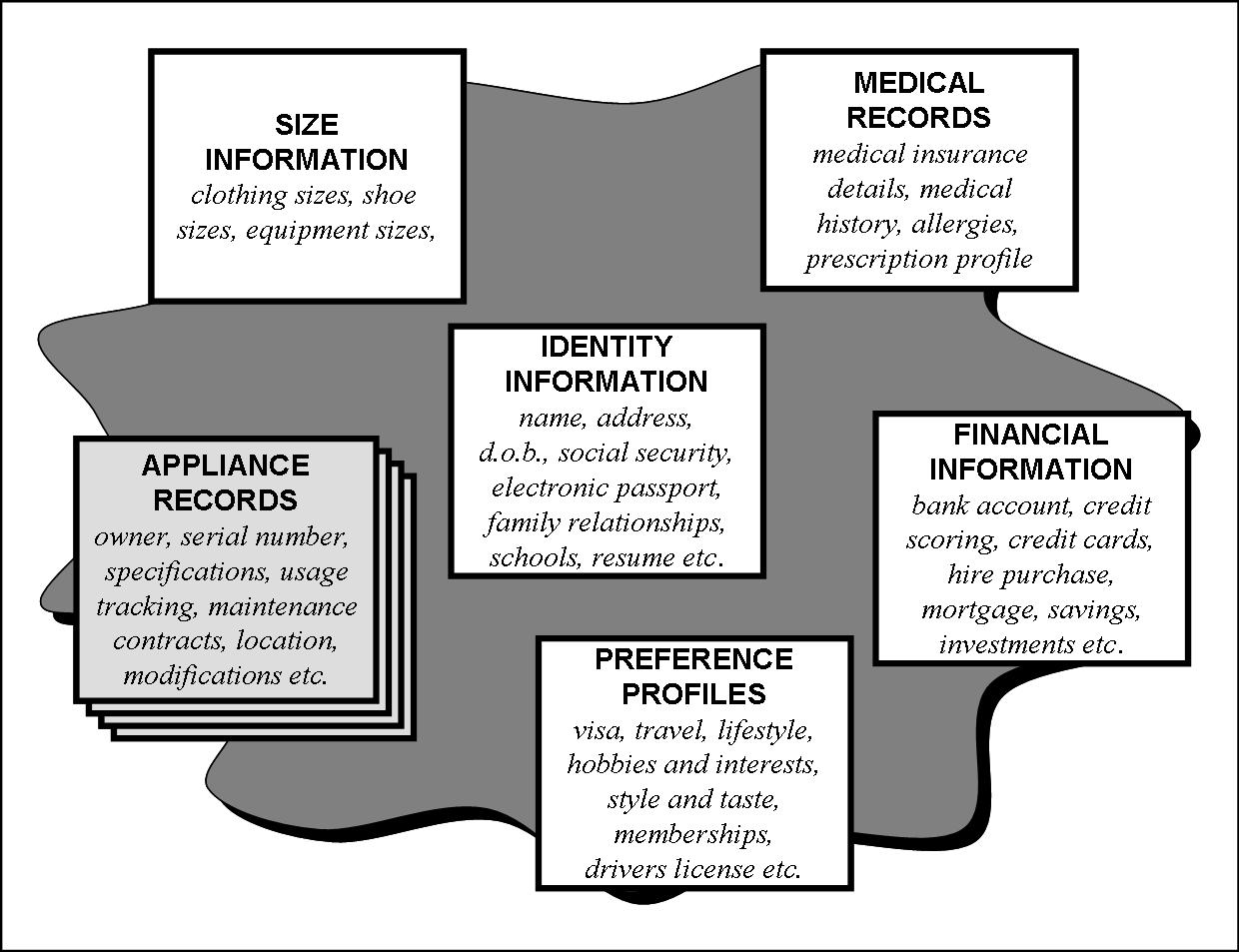
Volume
The volume of information about an individual that is digitally captured is increasing exponentially as the digital world approaches the physical world in terms of accuracy of information capture. Where once, information consisted of static records, this progressed to records of transactions, profiles built from socio-demographic data and captured actual behaviors.
Soon, every transaction, every movement and every expression of an individual's persona will be recorded, indeed this is almost the case today, but with the data being recorded by a number of different bodies. In addition to this, many of the appliances that an individual may own will be internet enabled and will be a further source of information.
Duplication
As the volume of information increases, it will become clear that many parties capture and maintain identical information about an individual. Organizations will begin to collaborate, creating single sources of information that are treated as a shared resource. For instance, insurance companies, auto-aftercare providers and motor manufacturers already share aggregated information about car ownership, however this could easily extend to the individual level.
Each party that the individual has interactions with is a source of information, which leads to the question of who owns items of information about an individual. Some of the information is clearly owned by the individual, however, other items can be owned by third parties who gain commercial advantage from it, this argument of shared versus proprietary will need resolution.
Accuracy
As the number of parties who create digital information and update individual's personal portals increases, there is an issue around who will be responsible for maintaining the information in an accurate state. Parties will need to ensure that the source of a change of state will be responsible for maintaining the information on the portal as current and accurate.
Privacy: access rights to personal information
How come there is an after-market for personal information is operated by organizations that have not been given explicit authority to maintain this information, leave alone broker it?
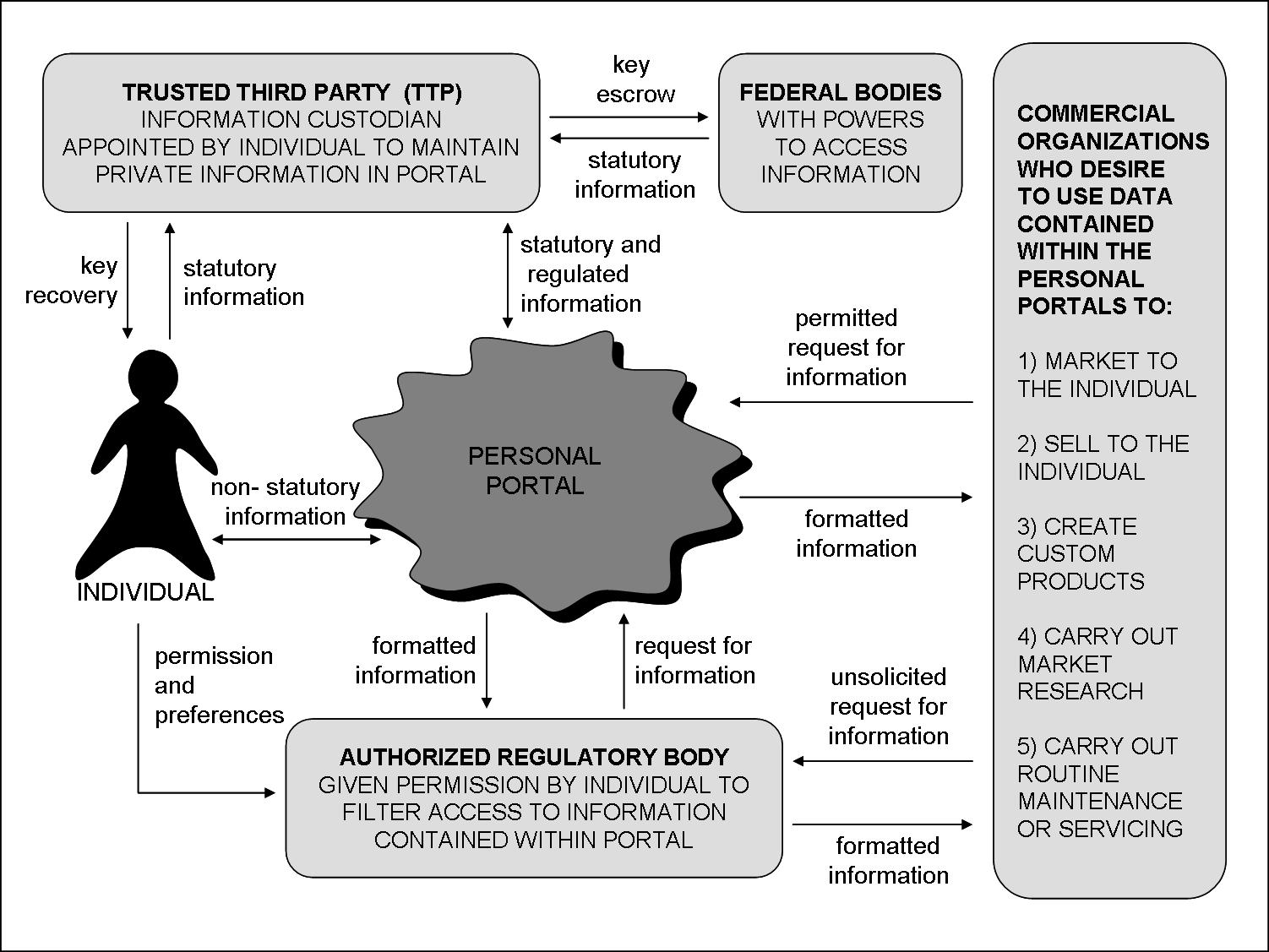
Request
The individual will allow a number of organizations to access certain public domain information about themselves (e.g. age, height, shoe size). If one such organization requires this information and the individual has already granted access rights the request will go directly to the personal portal. If the request is within the profile set up, the information is collated and sent out.
When an unknown commercial organization wants to access information about an individual for any legitimate purpose, it will send a request to the authorized regulatory body that has been authorized by the individual as a gatekeeper to the portal. Depending on the individual's profile, the request will be accepted or rejected. If rejected, the requesting organization may be able to apply for access. If accepted, the information would be collated and sent out.
There would also be a set of request types, requests for aggregated market research type information, one off requests for specific individual information, requests for regular information about an individual.
Certain federal bodies and other parties with the legal authority to access information would make their request to a trusted third party. Although these two parties would ultimately be federally controlled, they would fall under different administrative sections to maintain some control and privacy of information.
Permission
The individual would maintain a permission profile with the authorized regulatory body - this dictates which specific organizations can access information. This would be implemented by a hierarchy of levels of information: public domain (e.g. age) , private social (e.g. home address), private personal (e.g. income) and highly restricted.(e.g. medical history).
The individual would grant specific and generic access rights to different organizations for different time periods. A specific right may be to grant a clothing retailer permanent access to private social information. A generic right may be to grant all auto-manufacturers temporary access to income and driving habits while the individual is seeking to purchase a new vehicle.
The authorized regulatory body would also maintain a classification of organizations to make setting permissions easier for the individual. For instance the individual may simply say reject all requests from telco companies.
The regulatory body's business model would generate revenue from commission on information passed (from the requesting organization), from service charges to the individual and from aggregation and data analysis performed and sold to permitted organizations.
Security
If the information to be sent out is not public domain some form of encryption would be necessary. In such cases a private and public key system can be employed. The requestor would send the request encrypted in the individual's public key. Along with the request, the requestor would send their public key. The information would be returned encrypted using the requestors public key. In the case of organizations given access to sensitive levels, a custom key may be agreed between the two parties.
A different and more secure system should be employed for passing highly sensitive information to federal bodies with access rights. The trusted third party will act as a key Escrow agent between the individual and the government.
Individual Access
The individual will be able to access directly personal information, however, statutory information maintained by governmental bodies may only be accessed via the trusted third party. This would allow federal bodies to maintain confidential information about the individual.
Nominated Intermediaries
The role of the trusted third party responsible for maintaining federally restricted information would have to be a government agency set up with the sole intention of maintaining the individual information rights. This would mediate the argument between complete freedom of information (with no privileged rights for federal access) and a total police state (where all information can be accessed by government).
The role of the authorized regulatory body would be performed by an organization that has the trust and respect of the individual. This would create a number of players available to fulfill this position and it would be possible for a number of organizations to perform this task for an individual for different information types. For example an individual may nominate the American Marketing Association as gatekeeper for all unsolicited requests for marketing information and will nominate their own health insurance company as gatekeeper for all of their medical and genetic information.
Maintenance: keeping information current
Information about an individual should be maintained by the individual or by trusted appointees who have the knowledge, expertise and granted authority to maintain that information and how it should be used
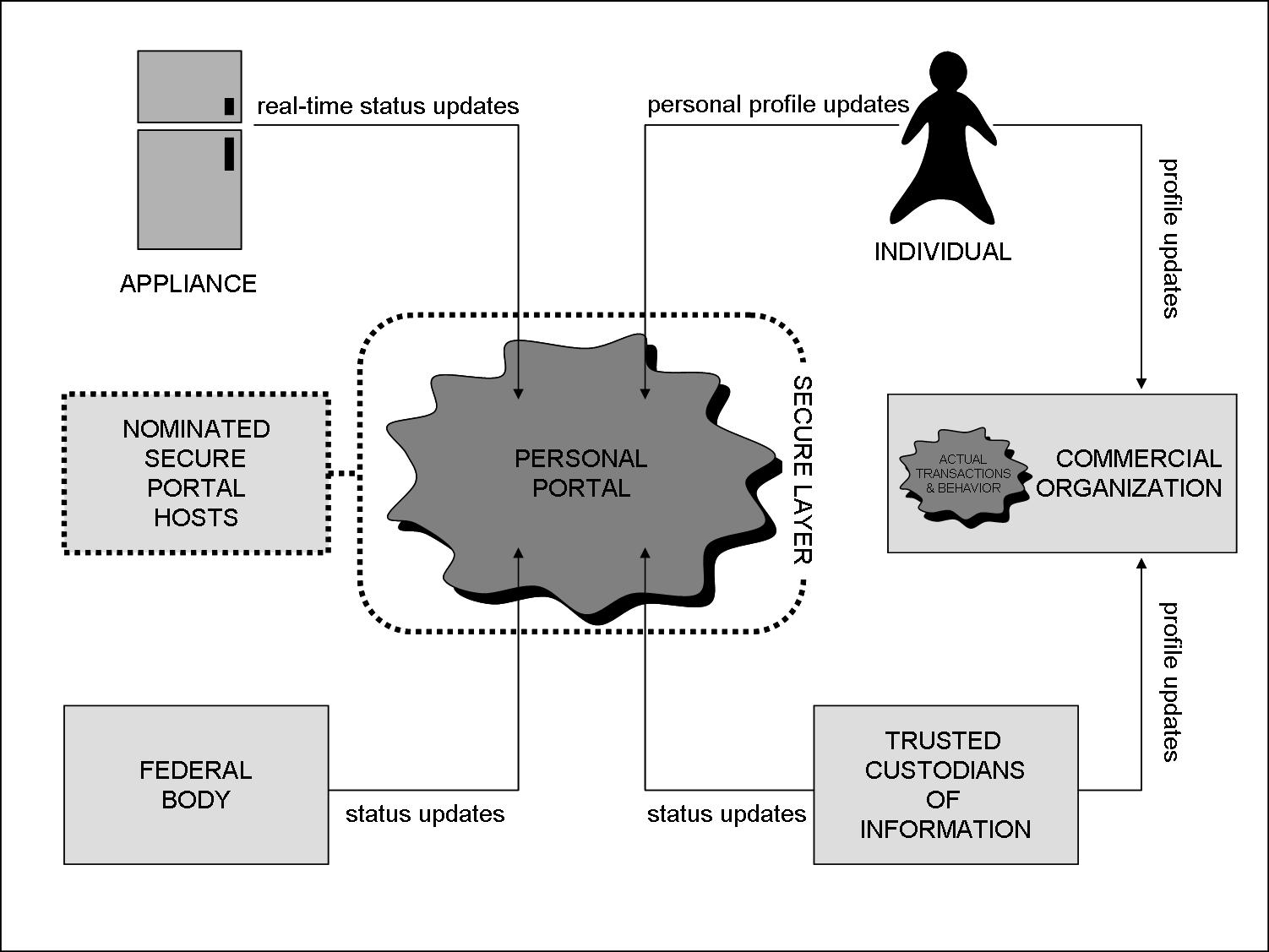
Individual
The individual will maintain key personal information such as names, preference profiles, calendars and social information such as references to contacts. (The contact information would be held as peer to peer (P2P) type references to the personal portals of other individuals). Much of the rest of the information that we would regard as personal today will be sourced directly from other parties in the future.
Appliance
Networked appliances would be able to maintain their own information on the portal for example, once an automobile is purchased, the dealer would transfer the information about it from its own record to the purchasing individual's personal portal. Whenever information about the car is generated then it would write it directly to the personal portal, for instance when the car is serviced, the mileage and service details would be written. When the car is sold on, these records are archived on the individual's portal, and also passed onto the next owner's portal. In this way, the car carries with it its own history. Also the driving history of the individual can be determined by examining all of the service records of the owner.
Trusted Custodian
Trusted custodians are organizations whom the individual appoints to maintain information on the personal portal. These would include such bodies as banks, personal accountants, employers, doctors, schools and universities. These would be able to directly update information on the personal portal.
Federal Body
Federal bodies such as INS, IRS and the Department of Justice would be able to maintain information regarding the individual on the individual's portal. There are security concerns here that information could be tampered with, however, it may be the case that information held at a secure portal host is more secure than in government storage.
Secure Portal Hosts
The success of the personal portal concept hinges on the secure portal hosts. Unlike other physically bound security systems the internet presents an open 'gamezone' to any hacker that wants to play. For every corporate security expert there are many individuals out in the world with the time and the motivation to beat them.
The secure portal host is expected to maintain the ring of security around the information and to manage the secure access mechanisms. This body must maintain themselves at the bleeding edge of internet encryption and other security measures. It must have a rigorous non-internet security policy in place to reinforce weaker links in the physical world.
Digital Rights Management (DRM) technology will probably play a part in the secure packaging of information and provision of access rights.
Commercial Organizations
Commercial organizations will generally regard information held about an individual as a source of competitive advantage (for this reason they will capture purchase histories and add these to aggregated psycho-demographic profiles). To maintain this, they would be able to keep their own information on an individual which would be supplemented by information on the personal portal (if they have been granted access rights by the individual). In this way they can be sure of having the most up to date information on any person.
24x7 Availability
The continuous and real time availability of information about the individual relies on personal portal availability being available real-time 24x7. Reference information such as a merchant accessing delivery addresses and bank details to fulfil a purchase would also require online access in real time.
Behavior: management of information
As each real-world entity takes its place on the web, it must gain a unique identity, characteristics and behaviors - when information gains behavior, then the internet will come of age.
The Information Content of Information
At the heart of the personal portal concept is the information entity. This is the object of importance or relevance that we wish to maintain information about. General database analysis techniques allow us to maintain identity and characteristics.
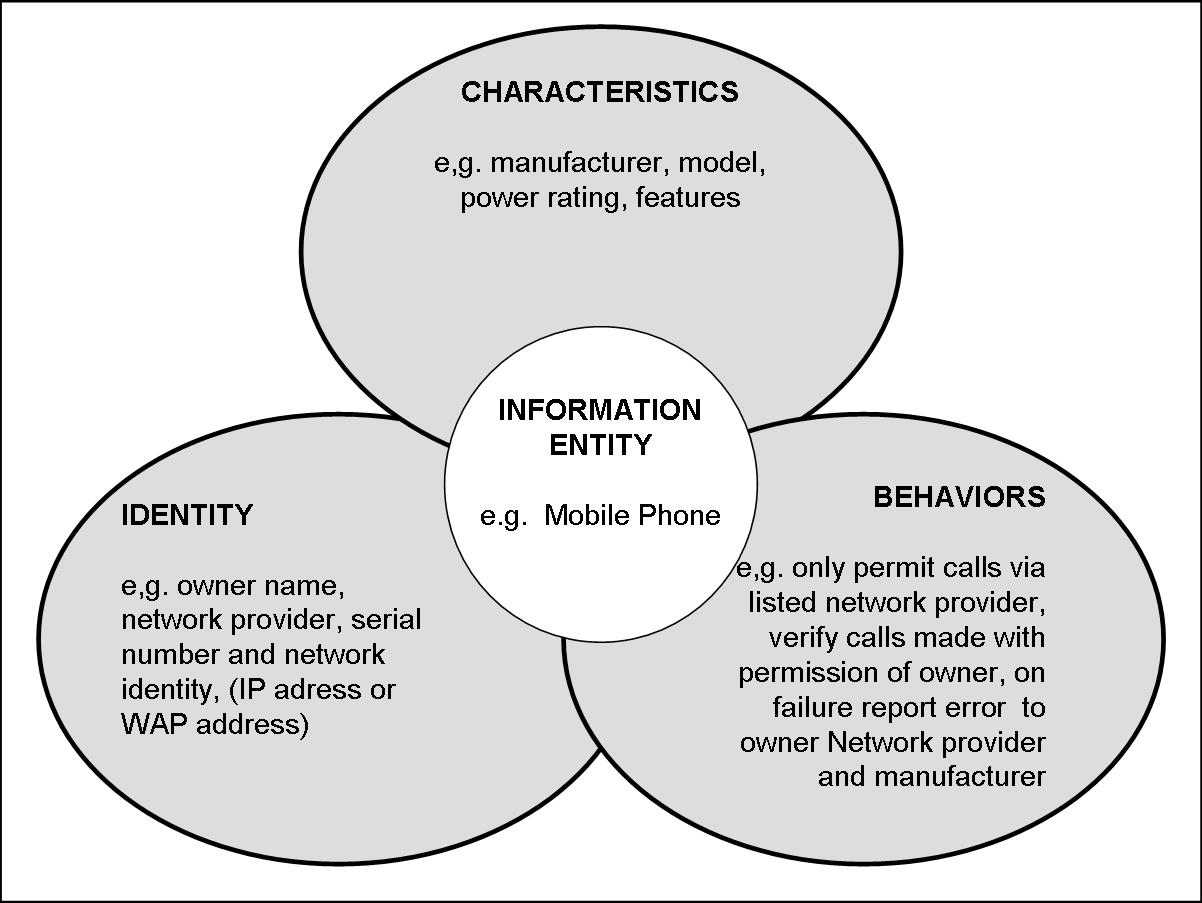
The identity is as unique as we need it to be - for a retailer the most specific level of a product, to identify a person a social security number, for a car, the registration number. Each organization may define its own unique key for an entity - for instance a mobile phone company will identify the SIM card number and the account number of the owner. Against each entity are held some characteristics - these will include physical, branding, and activity. Activity would include usage history, service history, fault records, ownership details etc.
Where the personal portal extends this concept is to also attach an information item a behavioral profile. This would allow trusted third parties and authorized regulatory bodies maintaining the information to automate information management tasks to a feasible level.
For example when I set up my new mobile phone, I would create a profile allowing billing information to be accessible to the mobile phone company, the bank and my work expenses account. The telephone number would be accessible to my friends and family and also to work colleagues. Directory enquiry companies would have to specify the identity and intent of an unsolicited number look up. Call location history would be highly restricted information as would outgoing calls - available only to myself and the mobile phone company.
eXtensible Markup Language (XML)
As most software development organizations have realized, XML and the 'tagging' metaphor provide the key to giving information meaning. The data definitions provided by versions of XML allow electronically held information to take on real world meanings, however, these definitions must be shared by organizations exchanging this information.
The personal portal is the 'hub' for information about the individual and by definition will become the place where organizations exchange information, so it is essential that standards for the meaning of this information are created, maintained and adhered to.
XML standards around each information entity should be defined as a joint activity by organizations using that information. These should be published as open standards and maintained by centralized bodies representing those most concerned with the accuracy of that information.
All three information types can be defined using XML:
Information Management Bodies
These bodies are responsible for the definition and management of the meta-information for the personal portal network and ensuring its smooth operation. The Peer to Peer (P2P) computing model used by the Internic for Domain Name Servers and popularized by Napster where individuals maintain the content for the network provides the most appropriate infrastructure for the implementation of personal portals.
Information management bodies (as previously suggested) should be open standards bodies run on a non-profit basis representing the commercial and non-commercial organizations who have an interest in the data. These will maintain the XML standards defining the data content of the personal portal and manage the network of physical storage facilities that make up each personal portal. (This may initially appear contrary to the concept of centralizing personal information that was discussed earlier in section 1.2, however, the physical and conceptual organization of information are two different matters).
Personal Portals: benefit summary
The internet is a network linking computers that maintain a representation of a segment of the real world. Every member of the real-world value chain stands to benefit from Personal Portals and the individual can once more regain control of their electronic persona.
Individual
For the individual the Personal Portal creates a single electronic point of contact for any party wishing to interact with him/her. This creates two immediate advantages: accuracy of information and security.
The accuracy of information is created by only having a single definitive version of information which can be accessed by all parties. The individual can ensure that this version is accurate and up to date (far easier than if this information is held multiple times and by many different bodies). Where the individual does not maintain personal information, third parties are appointed to do so - and this granting of permission ensures that there is responsibility and accountability for information accuracy. (These are all basic principles that corporations defined as information started to become a corporate asset.)
Security is an increasingly important consideration as more information becomes more accessible to more people. Today the individual is more vulnerable to disclosures of potentially sensitive information as more companies gather, store and disseminate personal data. The Personal Portal concept has an inherent security element whereby the individual has control over who accesses their information. This control is achieved by direct granting of access rights or by appointing a trusted third party to maintain access rights. The security, implemented by passwords and encryption, is as vulnerable to attack as any other secure information accessible via the internet. The intended development path will ensure that organizations with a commitment to maintaining a cutting edge position in internet security will be responsible for ensuring a 'secure perimeter' around each personal portal.
Commercial Marketing Organizations
Commercial marketing organizations can gain great advantages from the Personal Portal and in the same breath, if their marketing techniques rely on 'cheap tricks' and gimmicks may find the Personal Portal will thwart their marketing plans. There can be two main sources of advantage: the ability to create better targeted campaigns; and the opportunity to become a trusted intermediary.
The accuracy and permission nature of the portal will allow organizations marketing products that are of genuine interest to an individual to create a carefully targeted campaign. As the portal will allow a two-way interaction from the outset - where the individual is able to publish their profile and preferences - this can be accessed by the marketing organization and used to create a customized or personalized campaign. The permission nature will ensure that if the campaign does reach the individual the success rate is likely to be higher than for an unsolicited campaign.
For marketing organizations who are able to build a relationship of significant trust, they may be able to take this further and become the trusted intermediary for a segment of marketing communications. For instance a bank may be the trusted intermediary to filter out communications from marketers of big ticket items such as houses, cars and holidays.
Non-Commercial Consumer Representatives
Non-commercial organizations will also be able to take advantage of a relationship built on reputation and objectivity to become the trusted intermediary. The organization would take responsibility for filtering information from unsolicited marketeers and granting access rights on behalf of the individual. For example, the Consumer's Association may offer trusted intermediary services for the domestic and household segment managing communications from consumer packaged goods, household services and utility companies. Other potential candidates for this role would be industry bodies, consumer bodies, market intelligence organizations and web-portal operators, essentially any organization that can act as an objective filter between the internet open market and the individual.
There are two potential revenue streams for the trusted intermediary, the first being a standard fee payable by the individual who will receive mail filtering and the second by serving commercial marketing organizations with individual level and consolidated data.
Infrastructure Providers
The infrastructure providers are organizations who supply the foundations for personal portal technology. Starting at the bottom in terms of technology, the providers of database technology (e.g. Oracle), internet connectivity hardware (e.g. CISCO, Sun Microsystems), security (e.g. Intertrust), middleware providers (e.g. Vitria), the Application Service Providers who may host the portals and finally the applications software providers who will create the applications that are user by the individuals and end-user commercial organizations.
These organizations would benefit from the increased revenue from the use of their products in the creation of the personal portal network. This would require significant coordination between these parties due to the complexity of the interaction set between parties in the network and also due to the large critical mass of individuals required for this to actually work.
Federal Bodies
The federal bodies whose concerns include the maintenance of up to date records of individuals and also that of governmental security may stand to gain from the personal portal concept. If the electronically held information about the individual is left to evolve on its own, it will occur in many different locations. Holding it in one central (but virtual) location means that the government will be able to closely track the actions of an individual.
This may sound against all human rights arguments, however, this information is already there and available to those who know how to get it. The personal portal concept with a 'key escrow' system of security in place for both the government and the individual, allowing the individual the maximum amount of confidence that their information is protect and under the jurisdiction of a government organization set up to protect individual rights.